In this session Red Hat’s Ellen Newlines and Dmitri Pal discussed Red Hat's identity management portfolio from a near-term perspective, and presented the long-term roadmap—along with some advice for implementing identity management.
These are some highlights and quotable moments from the talk.
Identity management is complex but it’s something you need to do to protect your environment and, ultimately, the assets of your organization. Red Hat is focusing on making IdM automated and cost effective so that customers can focus on their business. It’s Red Hat’s job to provide the expertise.
The areas of vision:
Authentication
You need to be able to authenticate from different types of credentials including passwords, certificates, smart cards and OTP tokens. And use single sign-on using Kerberos, SAML, and OpenID connect. Weave together multiple operating systems, multiple credentials, multiple authentication schemes (including a trust relationship between IdM and Active Directory in a Microsoft environment).
Consistent Delivery
If you have consistency in the identities and access to them, you can deliver to systems, service
s, and applications together with policies to control access and privilege escalation. The goal is to make the use of this environment relatively seamless (even given the complexity).
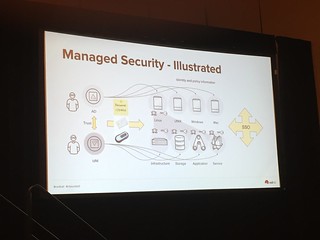
Managed Security
The challenge is the management of identities in a complex interoperable world. The keys, the certificates, the other secrets need to be automatically provisioned, tracked, and rotated on an as-needed basis.
DevOps Enablement
Developers need to have the tools to build the next generation of containerized and non-containerized applications with authentication and the consistent delivery of security. If the developer can’t do this, what they’re doing isn’t much use in a production environment.
Some guidance for identity management:
- Single source of identities. Don’t copy pass words around! It also makes it much easier for audit when identities are in a single place.
- Single sign-on is good. You need to protect the keys to the kingdom, but once you’ve established, use it as much as possible.
- Don’t put passwords into files. Instead use Kerberos or certificates, or fetch secrets on the fly. When you build applications and stitch things together, think about how they’re going to talk with each other. It requires a bit more effort but don’t be afraid to move forward.
- Automate your operations. We are in an era where changes are happening in real-time. Continuous integration and deployment of applications are needed to meet these business needs. Adopt the tools you need to do things in a simple, repeatable way. (For example, Ansible.)
- Integrate applications so that applications can interface with each other in the context of the user. These interactions need to be managed—which is where an IdM Fabric, as shown below, comes in.



No comments:
Post a Comment